Exploring the Advantages of Azure Terraform
As a software engineer at IntelliTect, I have found enormous customer benefits when developing and automating cloud infrastructure using Terraform. I love to learn, share, and teach about new and emerging technology. I especially enjoy discussing ways to help customers develop cloud solutions. I’ve found that development services that utilize Terraform deployments are a great way to help businesses run effectively and efficiently.
What is Terraform?
Terraform is an Infrastructure as Code (IaC) language that allows you to define, update, and maintain existing cloud infrastructure across major cloud providers, such as Azure, AWS, etc. Whether you are deploying a virtual machine, virtual network, Kubernetes cluster, or numerous other cloud resources, each resource’s configuration can be exact, repeatable, and easily updated as business requirements change within your organization.
This blog discusses the advantages of automating Terraform deployments using several approaches that provide security and maintainability. While I don’t discuss the intricacies of implementation, this blog explores what is possible through utilizing Terraform.
Automating Terraform Deployments
Terraform is a declarative language. Any desired resource configuration changes can be made to Terraform configuration files (also known as .tf files) and redeployed to update existing resources. While that may seem tedious on a resource-by-resource basis, you can create Terraform Modules to encapsulate common resource definitions and implement specific security requirements while leaving other settings varied. These customized modules encapsulate the resources that ultimately deploy to the desired environment.
Getting Started with Modules
In a traditional sense, you can think of modules as classes that can deploy infrastructure for your organization. Well-constructed modules are flexible and are reusable across deployment environments, such as Dev, Test, and Prod. Modules published to your organization’s source control can also be used to build complete cloud solutions by other developers.
Using a top-level configuration file, you can invoke the modules you wish to deploy in your environment. A significant advantage to this method for defining infrastructure is that you can automate deployments within your pipelines. This is only a small investment compared to the long-lasting benefits of such an implementation. Let’s walk through this with an example.
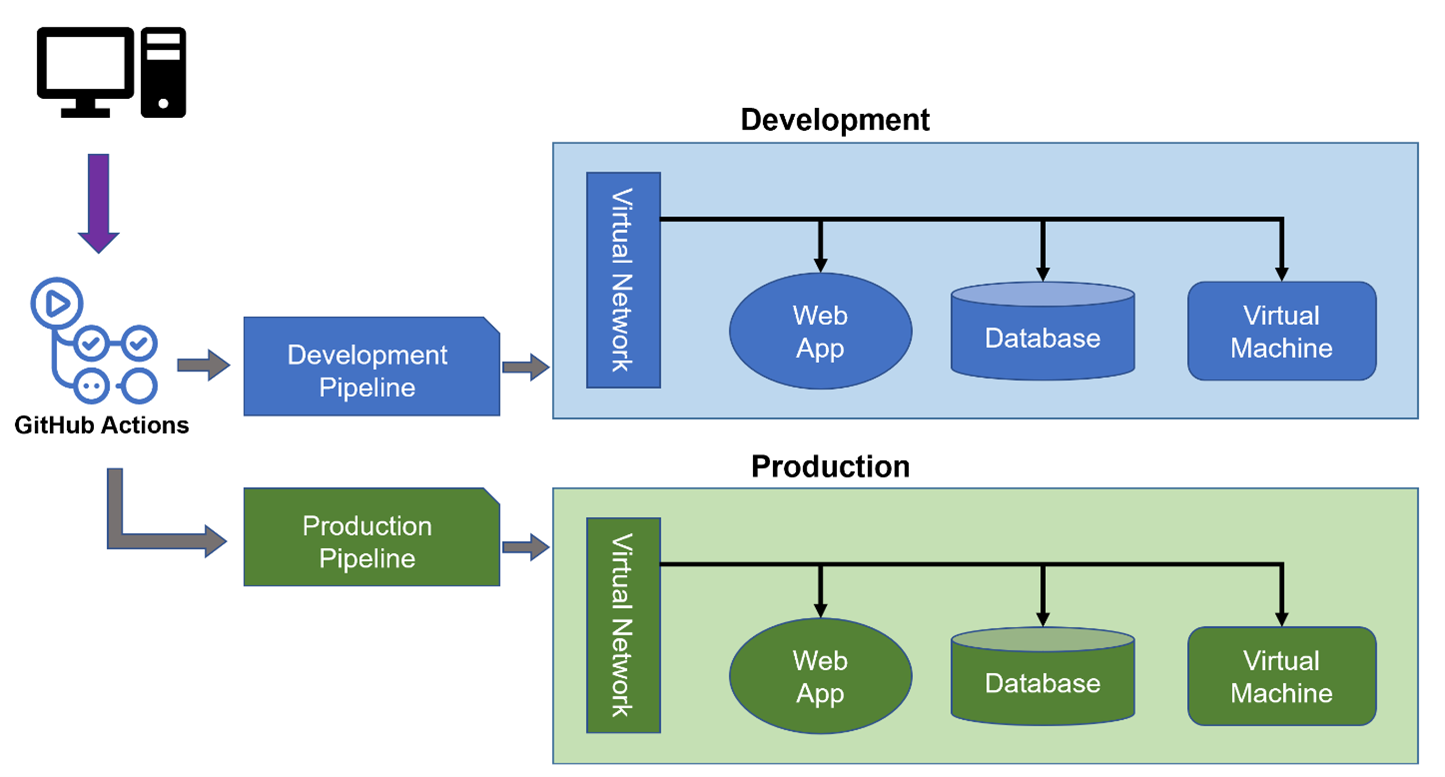
You can reuse this configuration repeatedly by using a top-level Terraform configuration file and defining all the resources you wish to deploy for a single environment, such as Development or Production. This main configuration can define any number of cloud resources to be deployed and can execute through a secured pipeline. The example shown above uses GitHub Actions. Still, other automation pipelines can serve the same function, such as Azure DevOps or other modern deployment tools.
It is also worth noting that by declaring this top-level configuration file and storing it in source control, you can test any infrastructure (or software) changes before altering your production environment. Additionally, many best practices can be used with pipeline resource deployments, such as requiring approvals or automating checks of infrastructure deployments to guarantee resources are not torn down and recreated during the deployment process without prior approval.
A Layered Approach
This simplified model can expand into multiple layers within each environment. The model splits deployments of different types of resources into categories, such as governance, networking, and application layers.
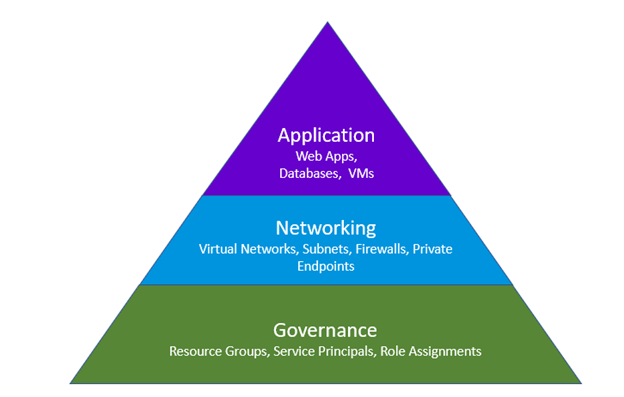
Using the same example environment mentioned earlier, the networking layer would contain resources such as virtual networks, subnets, firewalls, etc. The application layer would contain resources such as databases, web apps, and virtual machines. The governance layer could contain any base-level setup for your environment, such as resource groups, custom role-based access control (RBAC) roles and assignments, and creating service principals.
It is important to note that a layered approach is customizable to an organization’s needs. This approach may mean having more than three layers and deciding what purpose each layer serves to the cloud solution. Additionally, these layers should be determined based on the separation of privilege within the organization. For example, if a single development team is responsible for building and maintaining both the Application and Networking layers, it may be optimal to combine the two layers, given that the team will require access to both.
Why Use the Tiered Approach?
The significant advantage of this tiered approach is the separation of changes rolled out to a particular environment. This layered approach is beneficial for application deployments onto existing infrastructure, where it is far more secure to make changes to only the application layer of an environment rather than to all layers.
In the case of our example, it’s desirable to create a top-level Terraform configuration for each layer of the cloud solution, each calling to predefined modules for each service or set of services in the layer.
As changes need to happen to infrastructure, the top-level configuration file can be updated with those changes. Additionally, the file can be tested in the appropriate non-production environment and subsequently rolled out to the production environment once it has been verified and committed to main in source control.
The Future of Terraform In Azure
As it relates to the Azure cloud, Terraform has announced some exciting new features, such as Azure Terrafy.
Azure Terrafy provides a way to generate Terraform Templates based on existing resources already deployed to the cloud, whether manually or using various methods of automated deployments. Azure Terrafy allows the developer to manually configure or locate an existing resource (deployed any number of ways) and generate the template needed to deploy that exact resource.
Additionally, Microsoft has released a custom Terraform provider called AzAPI. AzAPI includes direct access to Azure APIs. This custom Terraform provider minimizes workarounds commonly needed to implement features not yet available natively with the Azure Terraform provider.
Wrapping Up
As the utilization of cloud solutions rapidly expands for large and small businesses, the surrounding technology is also swiftly changing. Terraform is one area where we are seeing this growth with its constant new features. The IaC language also can be utilized to create a secure and high-availability cloud environment.
Want More?
Want more information on Terraform? Check out Kevin Bost’s blog – Managing Infrastructure on Azure with Terraform, to learn more.
Need help creating a cloud solution? Connect with us through our contact page to explore how we can help you create a personalized cloud environment.

Does Your Organization Need a Custom Solution?
Let’s chat about how we can help you achieve excellence on your next project!
